Monitor Your Child's WhatsApp
Damien Gillett • April 27, 2021
What is WhatsApp?

WhatsApp is a messaging platform that has become extremely popular, more than 2 billion people in over 180 countries use WhatsApp. WhatsApp is free and offers simple, secure, reliable messaging and calling, available on phones all over the world. And yes, the name WhatsApp is a pun on the phrase What's Up. Facebook purchased WhatApp for a staggering $19 billion in 2014. So what, well due to it's popularity, ease of use and availability is has become the de-facto messaging platform for all ages. Well what does WhatsApp provide?
- Texts - Simple, Reliable Messaging
- Group Chat - Groups to keep in touch
- Voice and Video Calling
- Voice Messaging
- Photos and Videos
- Document Sharing
- Location Sharing
- End-to-end encryption
That sounds great, so why should I worry about my child's WhatsApp? Well it's not a matter of IF your child will end up on WhatsApp, but WHEN will your child end up on WhatsApp and HOW they will use WhatsApp.
Having a child that has recently received her own phone I have ensured parental controls are in place, screen time is limited and boundaries are set. We'll now highlight how you can ensure your child(ren) can use WhatsApp safely, some tips on how to introduce it to your child it and how to monitor your child’s WhatsApp.
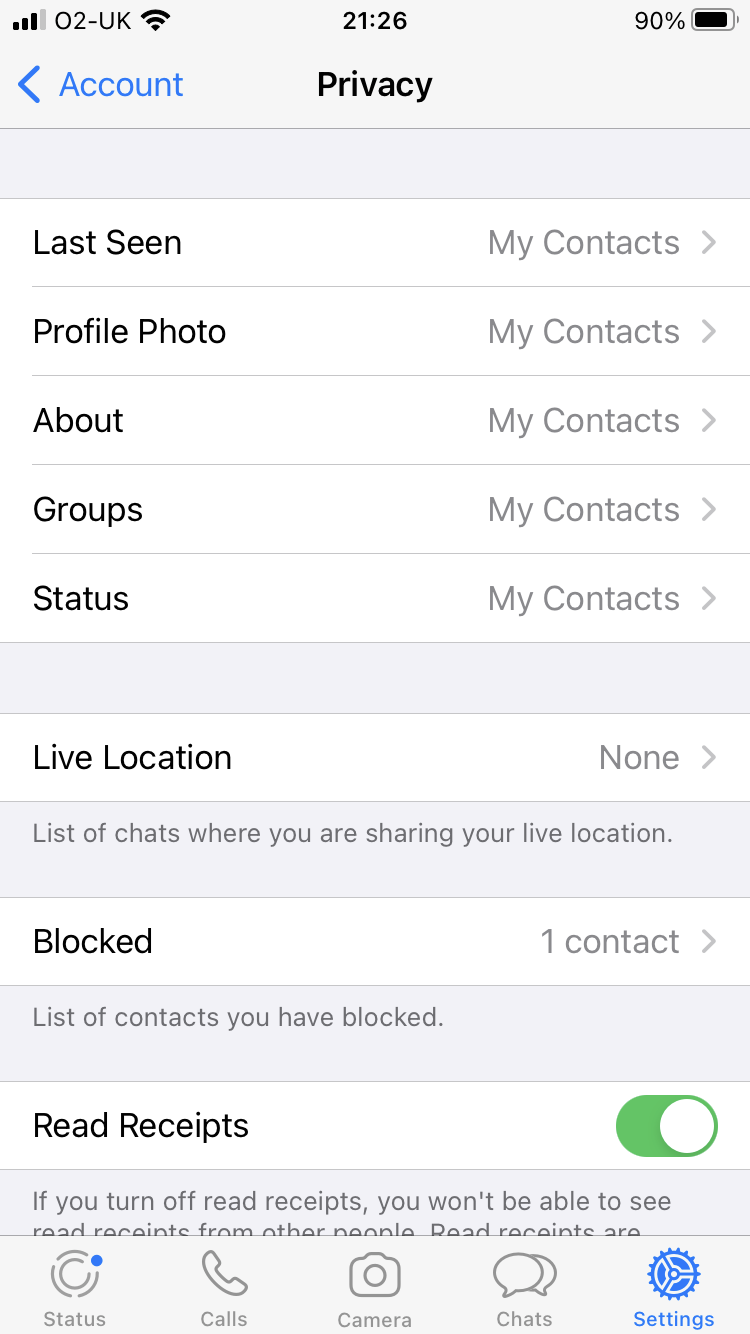
- With your child, review the WhatsApp Profile setting and select a picture that your child likes and you approve of. Following this go to Settings -> Account -> Privacy. You should ensure that as a minimum you set your child’s privacy settings to 'My Contacts'. The options here are 'Everyone', 'My Contacts' and 'Nobody', none of your child's Privacy settings should be "Everyone". Furthermore, you should restrict the 'Live Location' settings to 'None'
- Next select 'Two-Step Verification' and enable it. You will be required to provide a PIN and email address but in doing so you greatly increase the overall security of your child's account
- If utilising an Apple product you can also enable 'Screen Lock', this then requires 'Touch ID' to re-open WhatsApp and provides an additional layer of security to your child's account
How to monitor WhatsApp for Free:
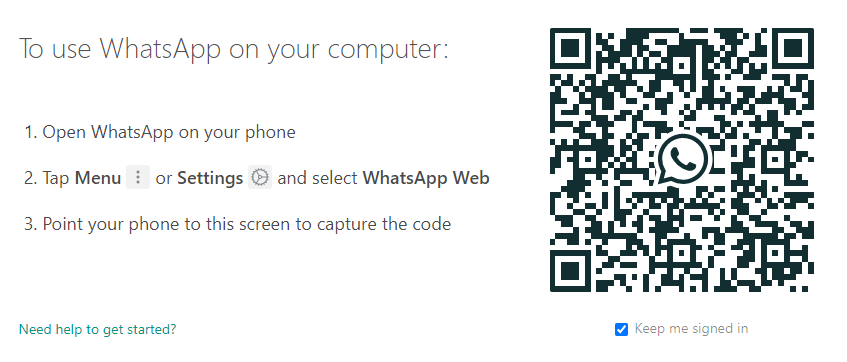
- On your home laptop or PC, browse to https://web.whatsapp.com/
- On your child's phone follow the instructions provided:
- Once synced you should be able to monitor chat history
Many may see this as being overprotective however, we must be open and honest with our children. There are online dangers such as bullying, sexting, pornography, stranger danger, etc. Therefore, it is essential to discuss with your child such issues:
- Teach your child to protect their WhatsApp account. Given that it doesn't require a password and unless you have set up 'Touch ID' your child may leave their phone unattended and unlocked. Someone may think it funny to send messages purportedly from your child. This may be harmless fun but may also have significant consequences if deemed inappropriate
- Has your child observed any foul language and if so could it be considered bullying? This should be discussed with your child to ensure that inappropriate behaviour is curtailed
- Sexting: Sexting is when you send a sexual message, photo or video to someone else. It could be a picture of you, but sometimes people send pictures and videos of other people. Learn more about sexting
- Fake News & Hoaxes: As adults we've become accustomed to 24/7 news and have a better grasp on what may be deemed 'fake news'. Children however, are likely to struggle with this concept at first. Have a conversation with your child about what is real news, what is fake
- Stranger Danger: Whilst we have set the Privacy settings to 'My Contacts' your child may innocently add a stranger to their contacts list. Therefore, it is still important to have a conversation with your child about stranger danger
- Finally, block WhatsApp before bedtime, set screen time. Apple devices are extremely easy to set up and it ensures that your child can get a good nights sleep
Should you wish to discuss this blog or any child online safety concerns please contact us at:
info@cybervio.co.uk

Cybervio is proud to announce that it has been awarded the prestigious Bronze Award in the Defence Employer Recognition Scheme (ERS). This accolade underscores our ongoing commitment to supporting the Armed Forces community and upholding the values of the Armed Forces Covenant. What is the Defence Employer Recognition Scheme (ERS)? The Defence ERS is a UK Ministry of Defence initiative that recognises employers who demonstrate exceptional support for the Armed Forces community. The scheme has three tiers—Bronze, Silver, and Gold—each reflecting increasing levels of commitment. The Bronze Award is granted to organisations that have pledged their support to the Armed Forces Covenant, making a tangible commitment to being Armed Forces-friendly employers. Cybervio’s Commitment to the Armed Forces Covenant At Cybervio, we recognise the invaluable skills and dedication that members of the Armed Forces bring to the civilian workforce. Our commitment to the Armed Forces Covenant is a testament to our support for: Promoting the Armed Forces Supporting Veterans Supporting National events & Armed Forces Charities Providing commercial support to members of the Armed Forces and Veterans who utilise our Services Why This Matters Earning the Bronze Award is more than just a recognition; it’s a reflection of our values as an organisation. At Cybervio, we believe in fostering a culture of respect, support, and opportunity for all, particularly those who serve or have served in the Armed Forces. By integrating these principles into our recruitment practices, workplace policies, and community engagement, we aim to set a standard for other employers to follow. Final Thoughts We are incredibly honoured to receive the Bronze Award and remain steadfast in our dedication to the Armed Forces community. Cybervio will continue to work hard to ensure that our workplace is inclusive, supportive, and empowering for those who have served our country. To learn more about our initiatives and how we support the Armed Forces community, visit our website or reach out to our team. Together, we can make a difference.
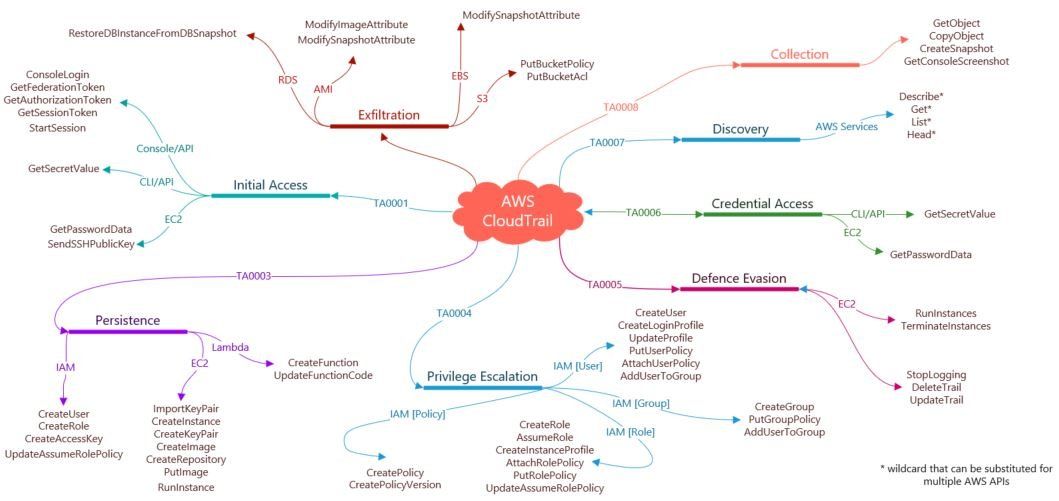
Whilst working in Cloud environments it is essential to understand what data sources are available to aid detection capabilities. In doing so, Blue Teams can align their monitoring in an attempt to identify potentially anomalous activity. One of the most useful sources of information whilst monitoring an AWS environment is derived from CloudTrail , this provides detail of any API calls made. The mindmap provides a useful resource for Blue Teams to aid detection capabilities, for example, an analyst may identify 'CreateUser' followed by 'CreateKeyPair', then followed by 'PutUserPolicy' or 'AttachUserPolicy' in conjunction with 'AddUserToGroup'. This identified activity would map to Mitre's ATT&CK framework, specifically, the Tactics Persistence and Privilege Escalation. Therefore, your Blue Team can utilise the mindmap in order to align detection capabilities to specific AWS API calls that map to ATT&CK Tactics and Techniques. Our previous blog post Sigmac: A Sigma to SIEM converter describes how a Blue Team can utilise Sigma rules, whilst making use of Pacu (an AWS exploitation tool) to create Use Cases and detection alerts to aid SOC analysts. Furthermore, the mindmap can be utilised to aid proactive threat hunting. There will likely be False Positives (FP's) in relation to the identified API calls as legitimate activity occurs within your environment. By utilising items such as authorised user/admin lists, standard operating hours and the principle of least privilege you can greatly reduce the overall amount of FP's. Overall, the mindmap can be utilised in a number a ways to enhance your security posture and reduce both the Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). Cybervio can assist your Blue Team in utilising the ATT&CK framework for Cloud in order to build detection capabilities against Tactics, Techniques and Procedures (TTP's) in an AWS environment.
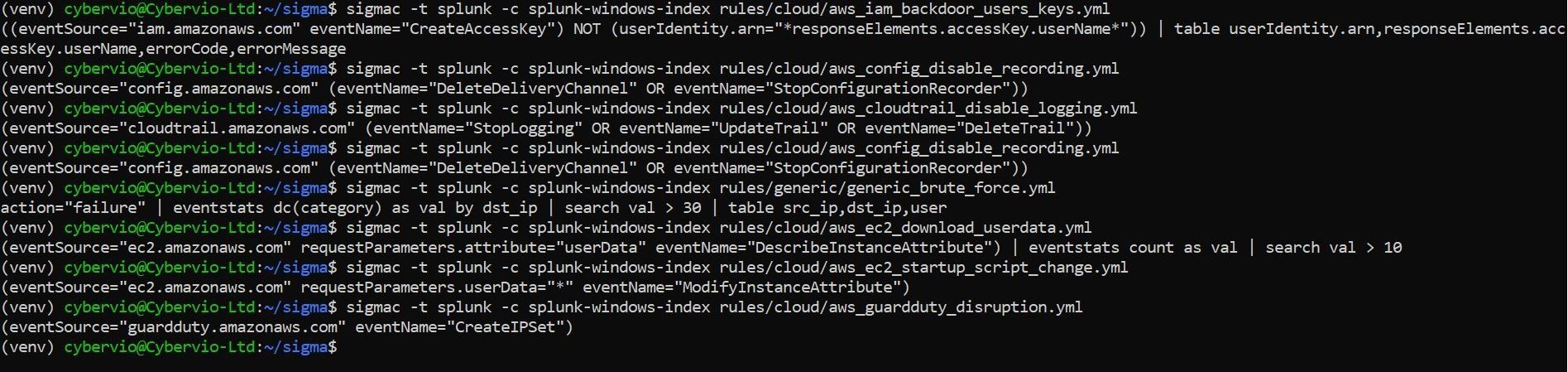
As @cyb3rops describes it, Sigma is an open standard for rules that allow you to describe searches on log data in generic form. These rules can be converted and applied to many log management or SIEM systems and can even be used with grep on the command line. Having been working through potential Splunk Use Cases and trying to take the viewpoint of an attacker I made use of the modules within Rhino Security Labs Pacu, an AWS exploitation framework. In doing so I came across Sigmac written by Florian Roth. In essence by utilising Sigmac you can take Sigma rules and convert them to a number of SIEM platforms, in this case Splunk. The setup, configuration and use is fully documented on Florian's GitHub page so I won't go into detail here. Essentially, by converting known, well documented Sigma rules into Splunk SPL you can aid detection of potentially anomalous activity within your environment. The resultant Splunk SPL search will likely require review for your environment, however, it will provide the basis to create useful content from. In doing so you can map Use Cases against exploitation frameworks, e.g. Pacu and detection frameworks such as ATT&CK.